Robot
red teaming
Robot
red teaming
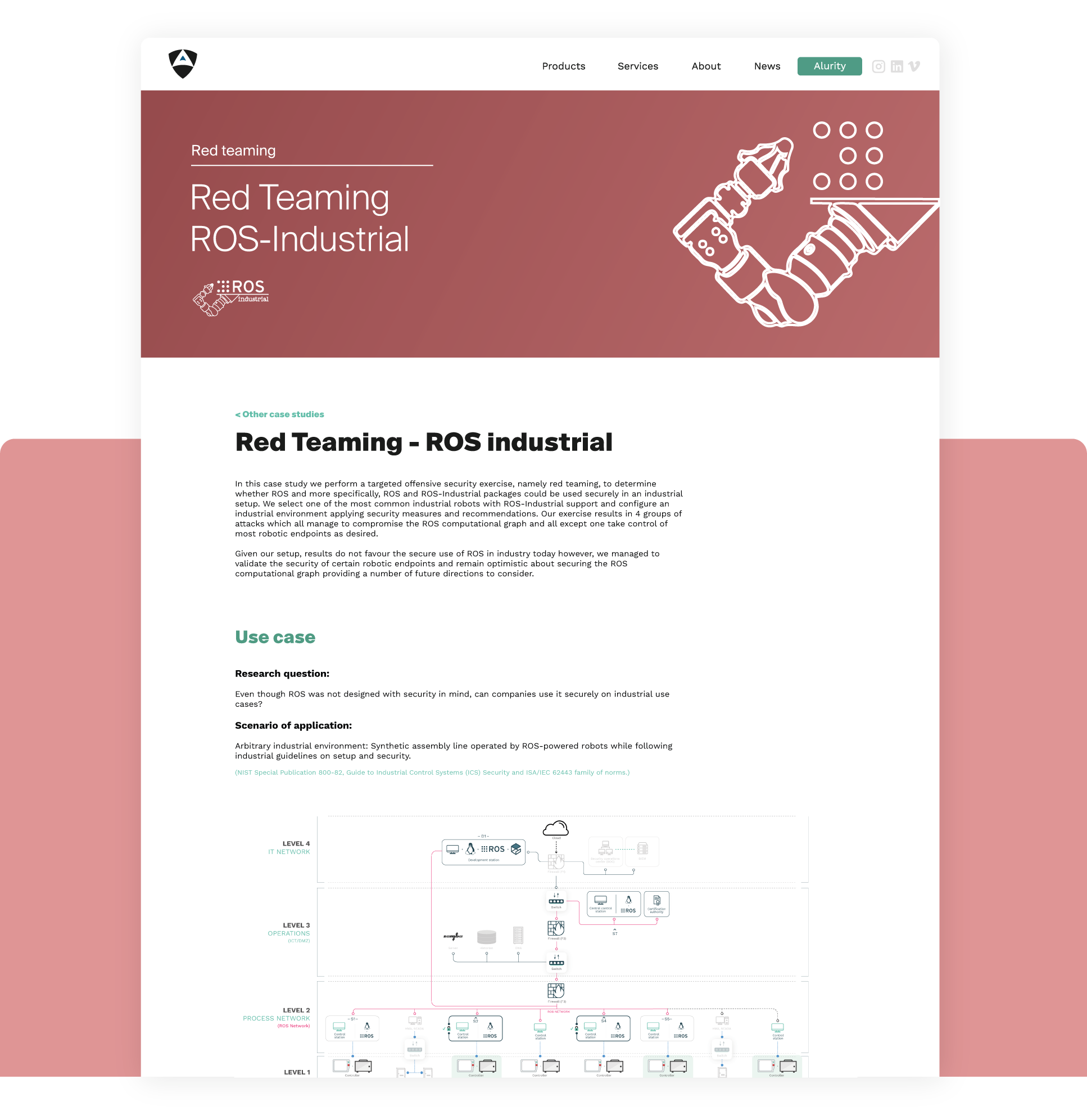
Full-scope and multi-layered targeted (with specific goals) offensive attack simulation designed to measure how well your robotic technology can withstand an attack.
This exercise produces an accurate measure of a given robotics technology’s preparedness for remaining resilient against cyber-attacks.
This type of assessment is generally performed in a black-boxed manner where Alias doesn't have access to additional resources except what's publicly available. Red teaming will look for vulnerabilities but only for those that will maximize damage and meet the selected goals.
See how it is done
Hire now!