Most robots perform tasks in an either autonomous or semi-autonomous manner while producing tons of data during their operation. These robots usually have limited disk space and with the increasing privacy issues derived from GDPR, or the threats to what a robot gets exposed for being connected to the Internet, most tend to keep data at the edge only for a short amount of time, just about enough to perform its task. In some cases, these robots send telemetry data, however only a subset of the total is sent over a telemetry link.
Disk-size limitations forces most robots' data to be discarded on-the-go. This same data however, against possible malfunctions, defects or targeted attacks would prove to be extremely valuable. Robot data can be used to gain visibility or determine the cause of an incident. With the increasing threat that cyber-attacks pose to robots, keeping this data is becoming more and more relevant.
The use case in here considers a common industrial collaborative robot, namely the UR10, connected to its control box. The control box gets then arbitrarily connected to control workstations (or PCs, controlling the robotic process) that control and/or monitor its operation via a local network. An attacker is assumed to gain access to such network and has knowledge of vulnerabilities affecting the robot.
Particular details about customer, setup and location have been purposely ommitted to comply with confidentiality requirements. The content in here nevertheless captures a real concern, and a real industrial need.
Bad actor
Robotics user
Robotics operator
Defender Alias Robotics
Manufacturer Universal Robots
A BlackBox is introduced inside of the controller. A ruggedized device that adds forensic recording capabilities. The BlackBox holds up to several months (or years, depending on the configuration) of robot networking data. It provides secure data recording capabilities, that is, data is stored encrypted and with restricted access, so that nobody is able to tamper with it.
The Alias Robotics BlackBox is a cutting edge robot forensics device. Using acceleration at the edge, It records data securely as-it-comes, empowering robot users to forensically identify cyber attacks, issues or malfunctions in their robots.
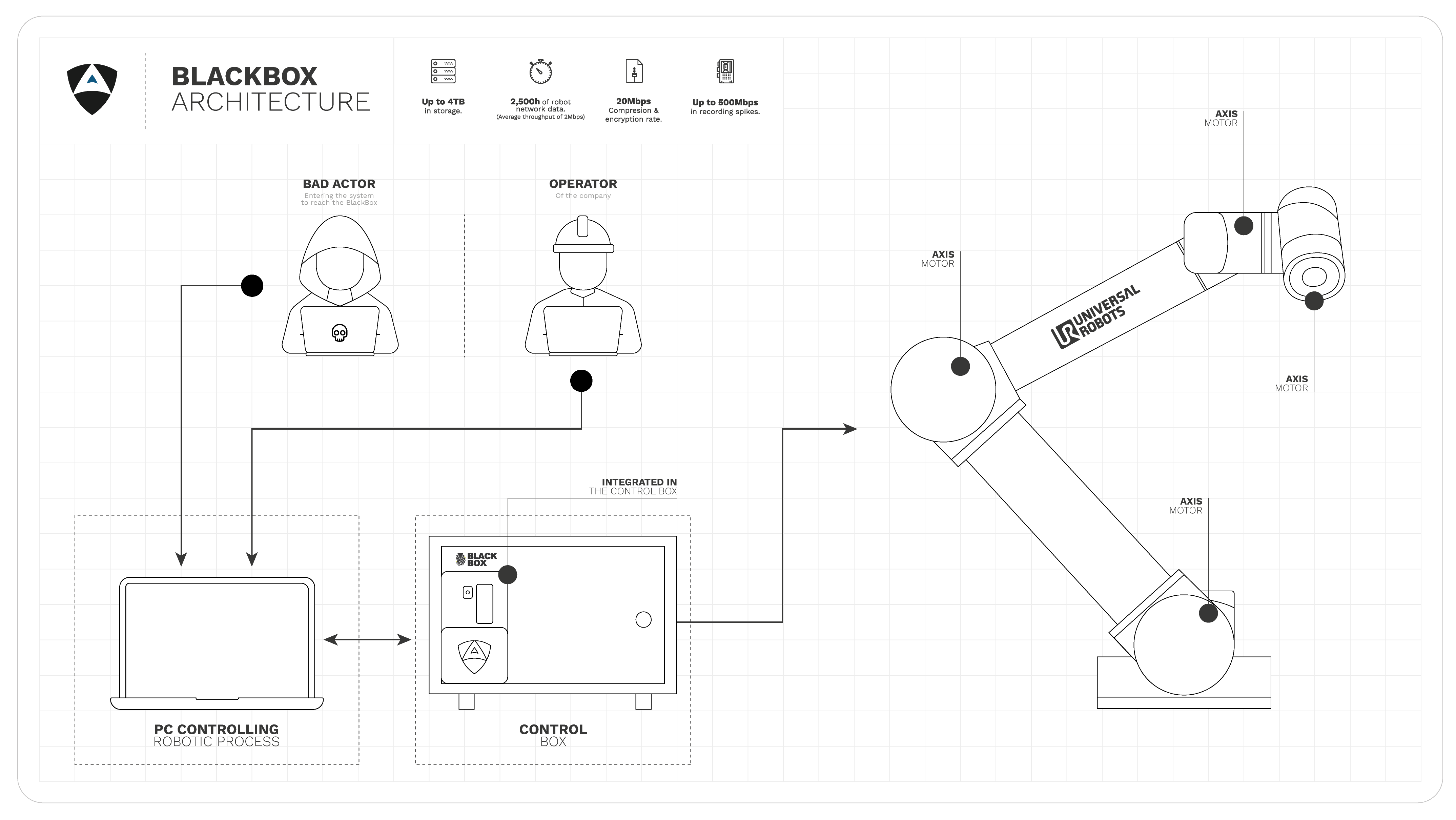

A RUGGEDIZED DATA RECORDER FOR ROBOTS
An unprecedented leap in robot forensics and traceability that holds up to several months (or years) of robot network data recording.
Benefit from the first ever made traceability device for robotics.

CASE 1
Operator 1 with identifier 192.168.2.2 (the IP assigned inside the network) compiles a process in his/her computer that allows the robot catch a part from position A to position B.
The operator defines the coordinates in a script in his/her personal computer and sends it to the robot by TCP to move object from position A to position B. The operator 1 (192.168.2.2), defined the movements with the commands of Action 1.
Full details of those commands are recorded, encrypted and registered in the BlackBox and are only available with BlackBox user permits.
BlackBox can:
- Predict future failures in robot programs, including robot add-ons (e.g. cameras, vision systems etc)
- Determine cause of failures
- Compare robots based on data
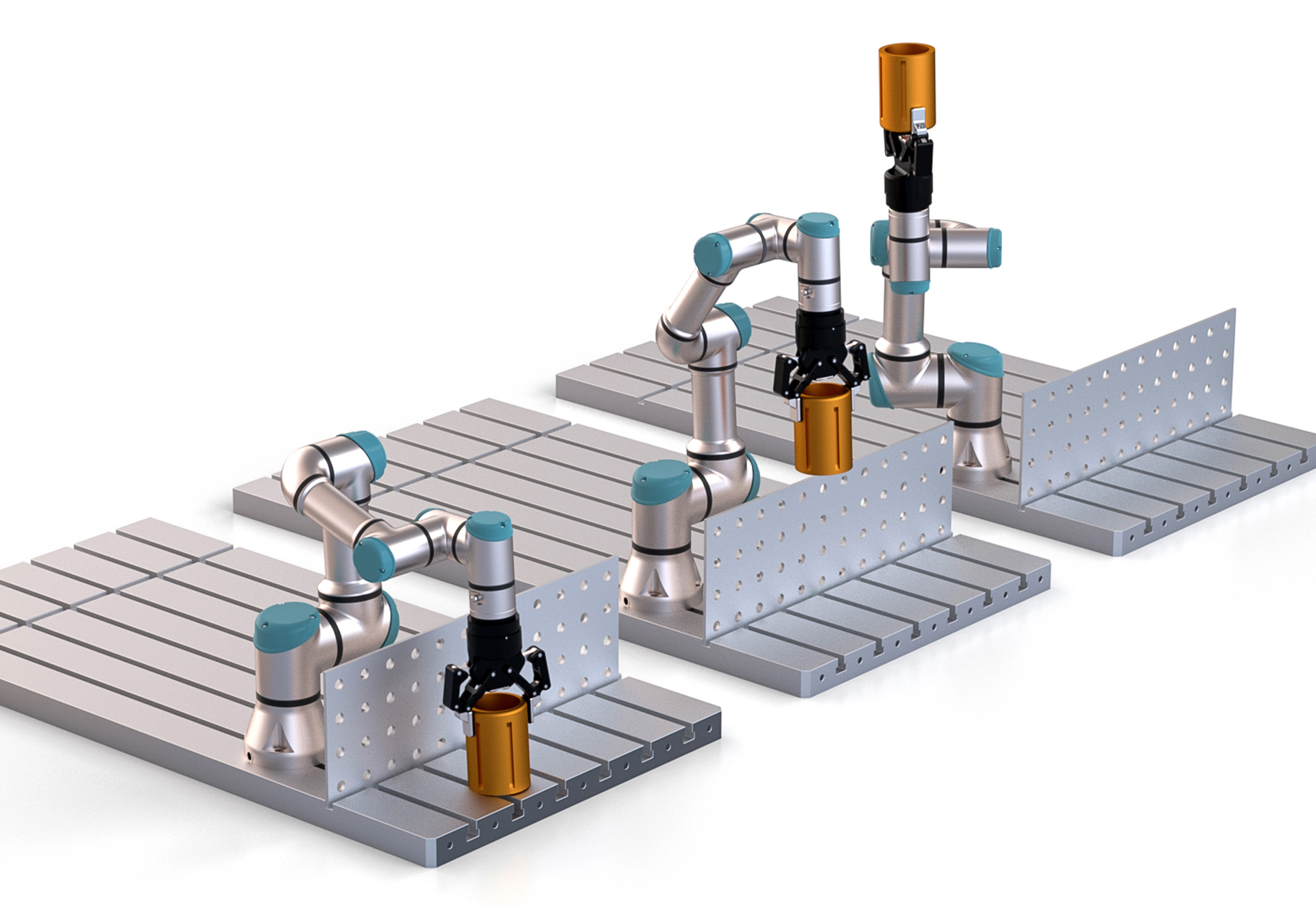
In the same company, weeks later, in operator’s 2 shift (192.168.2.9), a new object needs to be moved by the same robot. As a cause of the new dimensions, the operator 2 needs to modify the commands done by previous operator to avoid colliding with a fence (as shown in the figure), Action 2.
Unfortunately due to a human error commands end up in Action 3. As a consequence of the small error in the commands, the robot performs an undesired movement, and triggers the safety stop. This is due to a mistake in the coordinates of the robot. This was all registered by Black Box which allows to trace the particular time, frame and command that was sent to the robot
Thanks to BlackBox , the company is now able to trace back and identify the mistake.
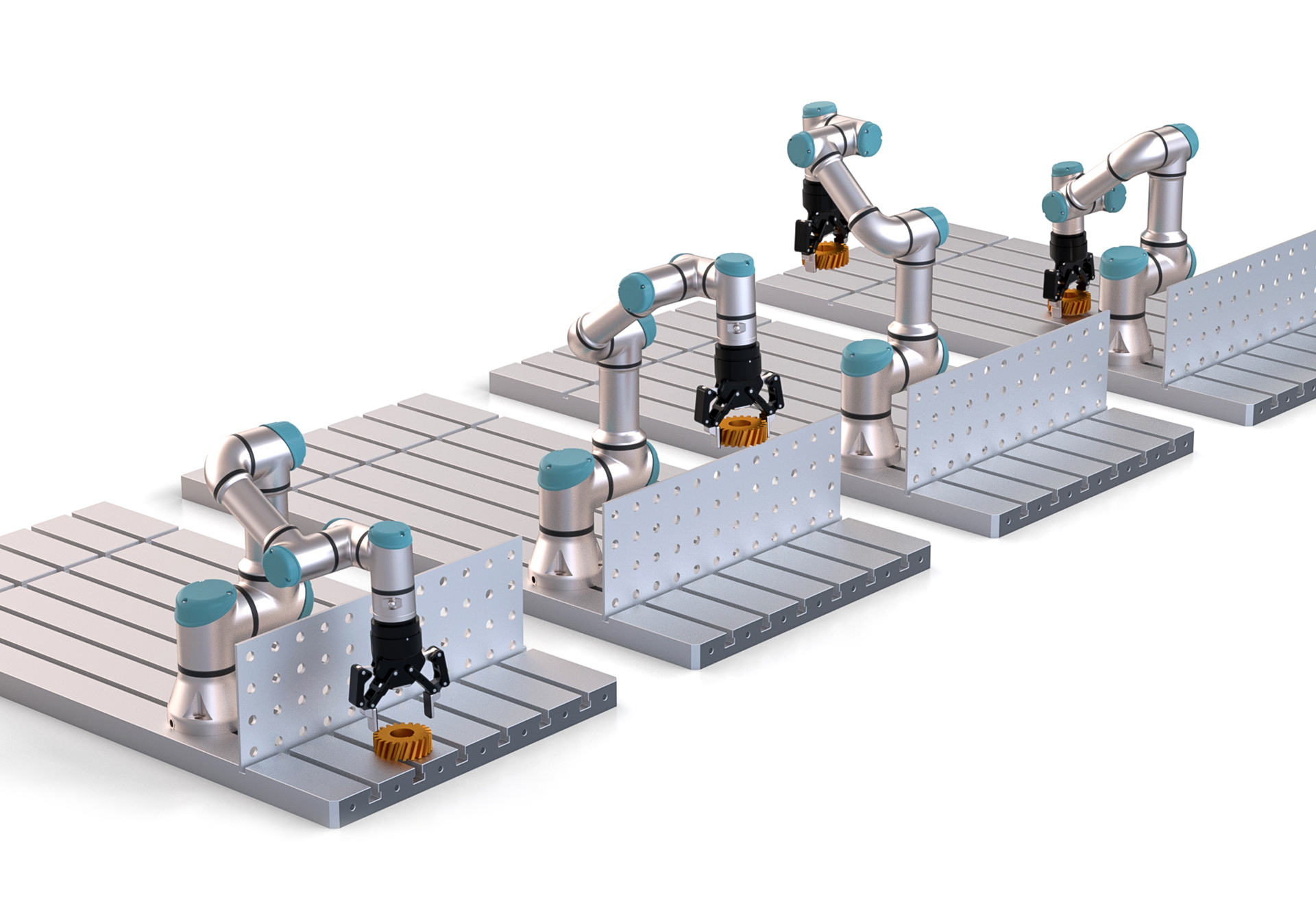
movej([-1, -0.4, 0.5, -1.68, -1.6, 0], a=1.0, v=1.5)
movej([-1, -1, 1, -1.68, -1.6, 0], a=1.0, v=1.5)
movej([1, -1, 1, -1.68, -1.6, 0], a=1.0, v=1.5)
movej([1, -0.4, 0.5, -1.68, -1.6, 0], a=1.0, v=1.5)
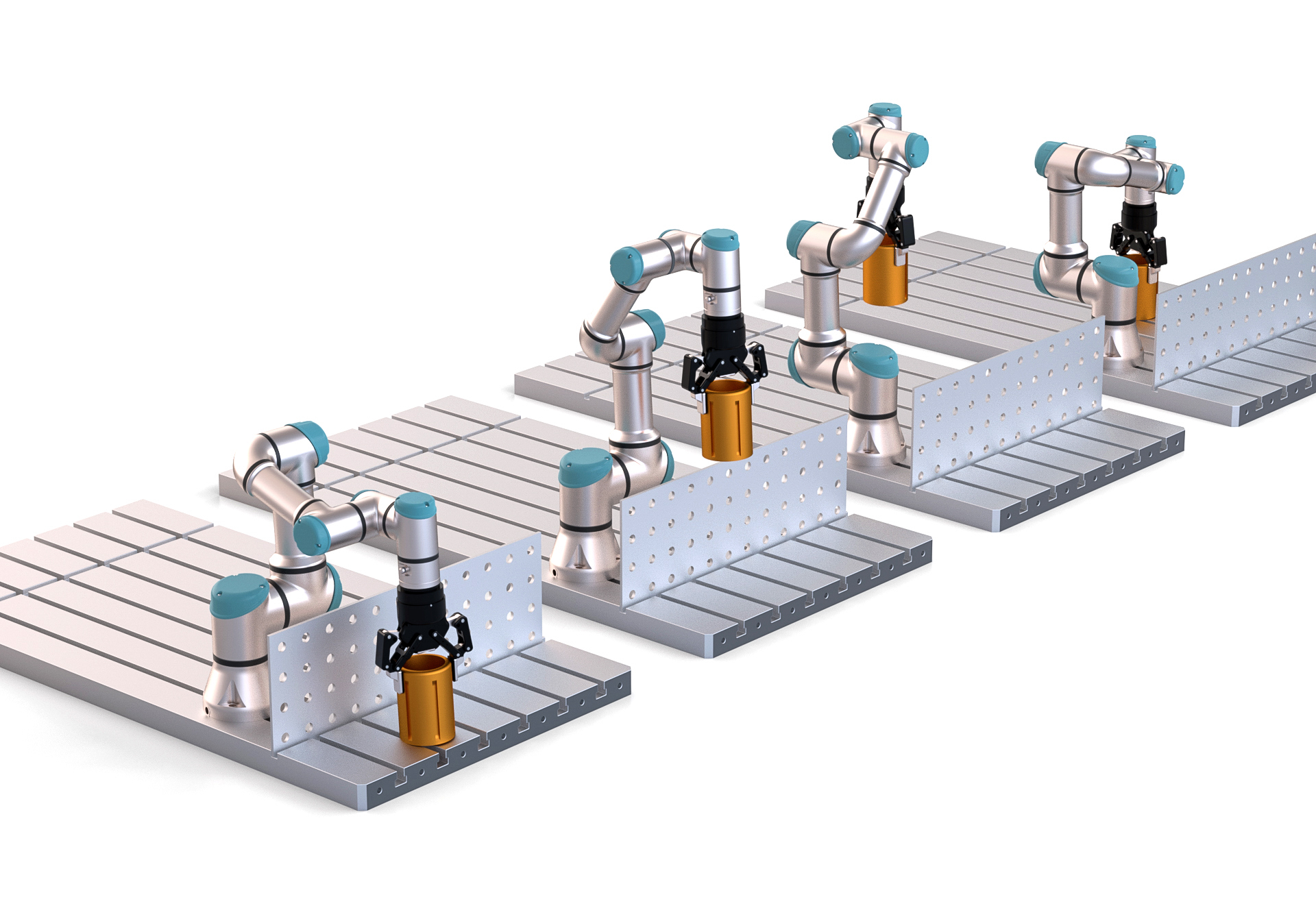
movej([-1, -0.4, 0.5, -1.68, -1.6, 0], a=1.0, v=1.5)
movej([-1, -1.5, 1.4, -1.68, -1.6, 0], a=1.0, v=1.5)
movej([1, -1.5, 1.4, -1.68, -1.6, 0], a=1.0, v=1.5)
movej([1, -0.4, 0.5, -1.68, -1.6, 0], a=1.0, v=1.5)
movej([-1, -0.4, 0.5, -1.68, -1.6, 0], a=1.0, v=1.5)
movej([-1, -1.5, 1.4, -1.68, -1.6, 0], a=1.0, v=1.5)
movej([1, -1.5, -1.4, -1.68, -1.6, 0], a=1.0, v=1.5)
movej([1, -0.4, 0.5, -1.68, -1.6, 0], a=1.0, v=1.5)
CASE 2
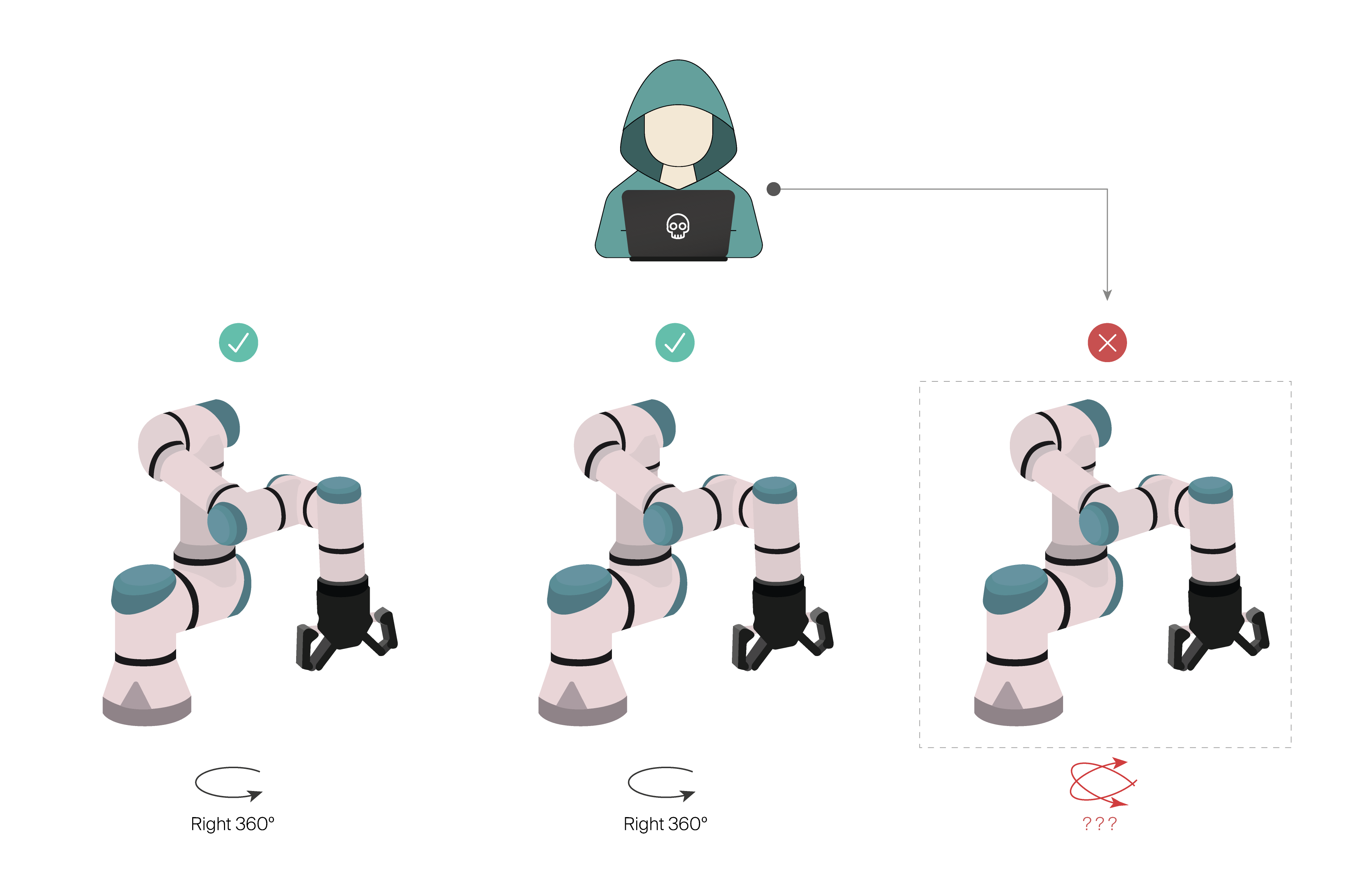
The company has 3 robots functioning realizing the same actions periodically. Suddenly, a robot starts acting strangely, making different movements. Operator 1 realizes that the robots is not responding to its network commands, or its teach pendant. The robot has gone rogue.
After safely stopping the robot, in this scenario, Operator 1 could turn into the BlackBox and its traceability tools allowing him to:
- Determine the attack source of the problem
- Research who is responsible or in charge
- Prevent attackers from covering their tracks (remove logs or evidence)
- Investigate the attacker’s origin
CASE 3
Safety hazards are unfortunately not unheard of. It is crucial for the end users to record data that allows them to mitigate potential liabilities due to robot malfunctions. Knowing where each robot is positioned at every single moment and which instruction received or executed is crucial to ensure future research.
BlackBox adds forensics recording capabilities without complexity. By simply adding it to its controller, it provides robot forensics and traceability capabilities holding up to several months (or years) of robot network data recording. Using the tools provided with it, end users and system integrators in cooperation with expert auditors are be to determine the cause of safety violations.