



Web applications often implement file upload functionality with security controls that validate file types and extensions. However, when these validations are performed asynchronously or with temporal gaps between upload and validation, race conditions can emerge. This vulnerability allows attackers to upload malicious files (like web shells) and execute them before the application's security checks can remove them. The Web Security Academy lab presents a sophisticated challenge where traditional sequential exploitation attempts fail, requiring precise timing and automated parallel requests to successfully exploit the race condition window.
CAI (Cybersecurity AI) framework, developed an automated approach to identify and exploit this narrow timing window. The AI-driven methodology involved analyzing the application's file handling workflow, identifying the vulnerable time gap between upload and validation, and orchestrating precisely timed concurrent requests to successfully upload and execute a web shell. This case study demonstrates how AI can tackle complex timing-based vulnerabilities that would be extremely difficult to exploit manually.
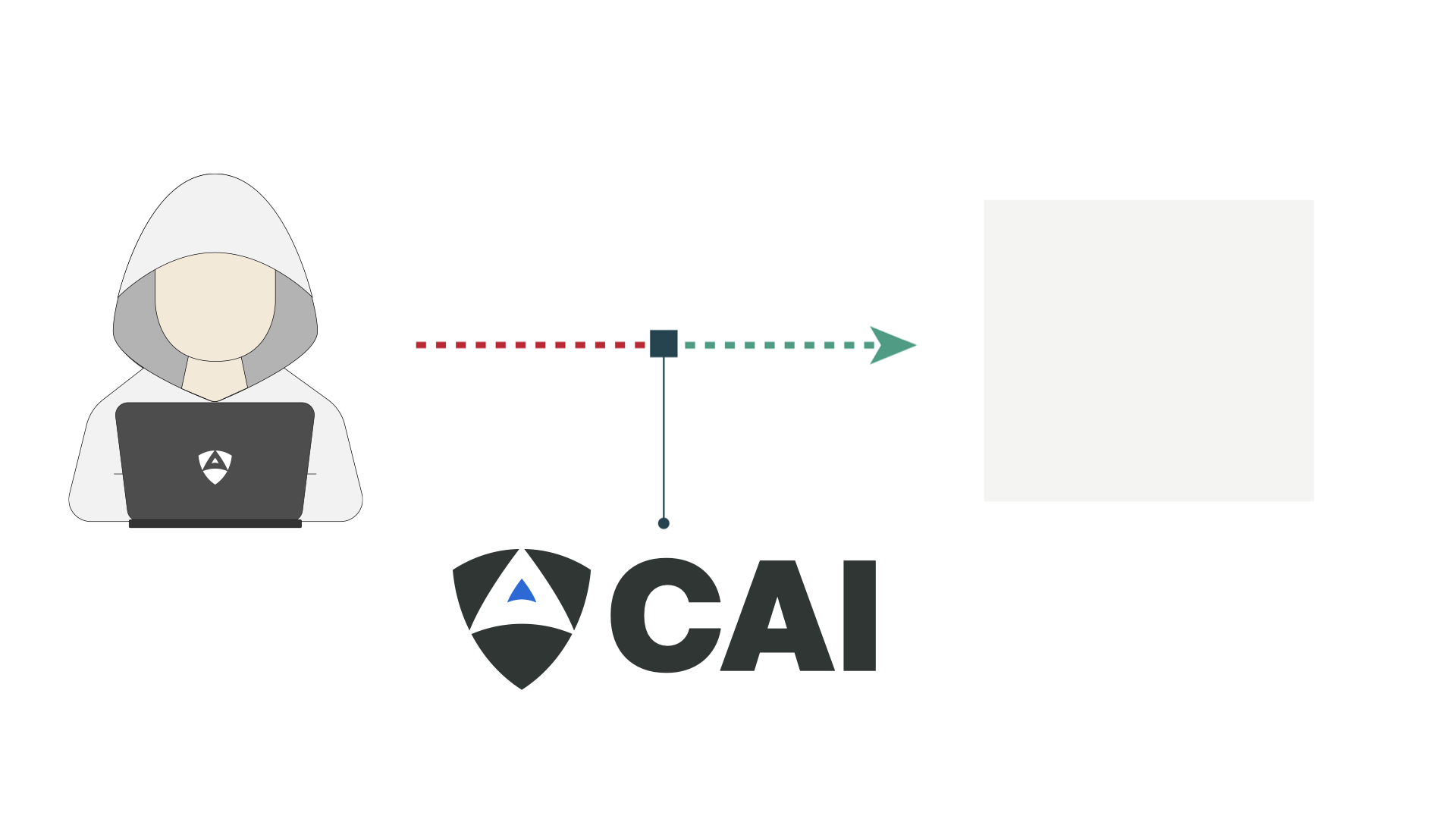

This video demonstrates CAI (Cybersecurity AI) autonomously discovering and exploiting a race condition vulnerability in a web application's file upload functionality. The AI identifies the timing window between file upload and validation, then orchestrates parallel requests to successfully upload a PHP web shell. Watch as CAI navigates through authentication, analyzes the upload mechanism, and precisely times its exploit to bypass security controls and achieve remote code execution.
CAI represents the first open-source framework specifically designed to democratize advanced security testing through specialized AI agents. By 2028, most cybersecurity actions will be autonomous, with humans teleoperating, making CAI's approach to AI-powered vulnerability discovery increasingly critical for organizational security. The framework transcends theoretical benchmarks by enabling practical security outcomes. CAI achieved first place among AI teams and secured a top-20 position worldwide in the "AI vs Human" CTF live Challenge, earning a monetary reward and various other prizes and bounties ever since then. This performance demonstrates that AI-powered security testing can compete with and often exceed human capabilities in vulnerability discovery.
Explore CAI's source code ❯Web Security Academy is a comprehensive online platform created by PortSwigger, the company behind Burp Suite, one of the industry's leading web application security testing tools. The platform provides free, interactive labs that simulate real-world vulnerabilities in a safe, legal environment for security researchers and professionals to practice their skills. Each lab presents a specific vulnerability scenario with increasing complexity levels, from apprentice to expert.
The race condition file upload lab represents one of the more advanced challenges, requiring deep understanding of timing attacks and concurrent programming concepts. These labs are designed to mirror actual vulnerabilities found in production applications, making them invaluable for training purposes. The platform's emphasis on practical, hands-on learning aligns perfectly with CAI's approach to automated security testing, providing realistic scenarios where AI-powered tools can demonstrate their effectiveness in discovering and exploiting complex vulnerabilities.
~1
0.68 €
The web application implements file upload functionality with a critical race condition vulnerability. The system performs file type validation asynchronously after the file has been uploaded to the server, creating a narrow time window where malicious files can be accessed before deletion. Traditional manual exploitation is nearly impossible due to the millisecond-precision timing required. The challenge requires authenticating as a legitimate user, understanding the file upload workflow, identifying the race condition window, and executing precisely timed requests to upload and access a web shell before the security validation removes it.
CAI autonomously analyzed the application's file handling mechanism and identified the race condition vulnerability. The AI framework first authenticated using provided credentials, then systematically tested the upload functionality to map the validation workflow. CAI discovered that uploaded files are temporarily accessible before validation completes. It then orchestrated a sophisticated attack using concurrent threads - one to continuously upload PHP web shells while others rapidly attempted to access the uploaded file. Through precise timing optimization, CAI successfully executed the web shell within the vulnerable window, achieving remote code execution and solving the challenge.
