



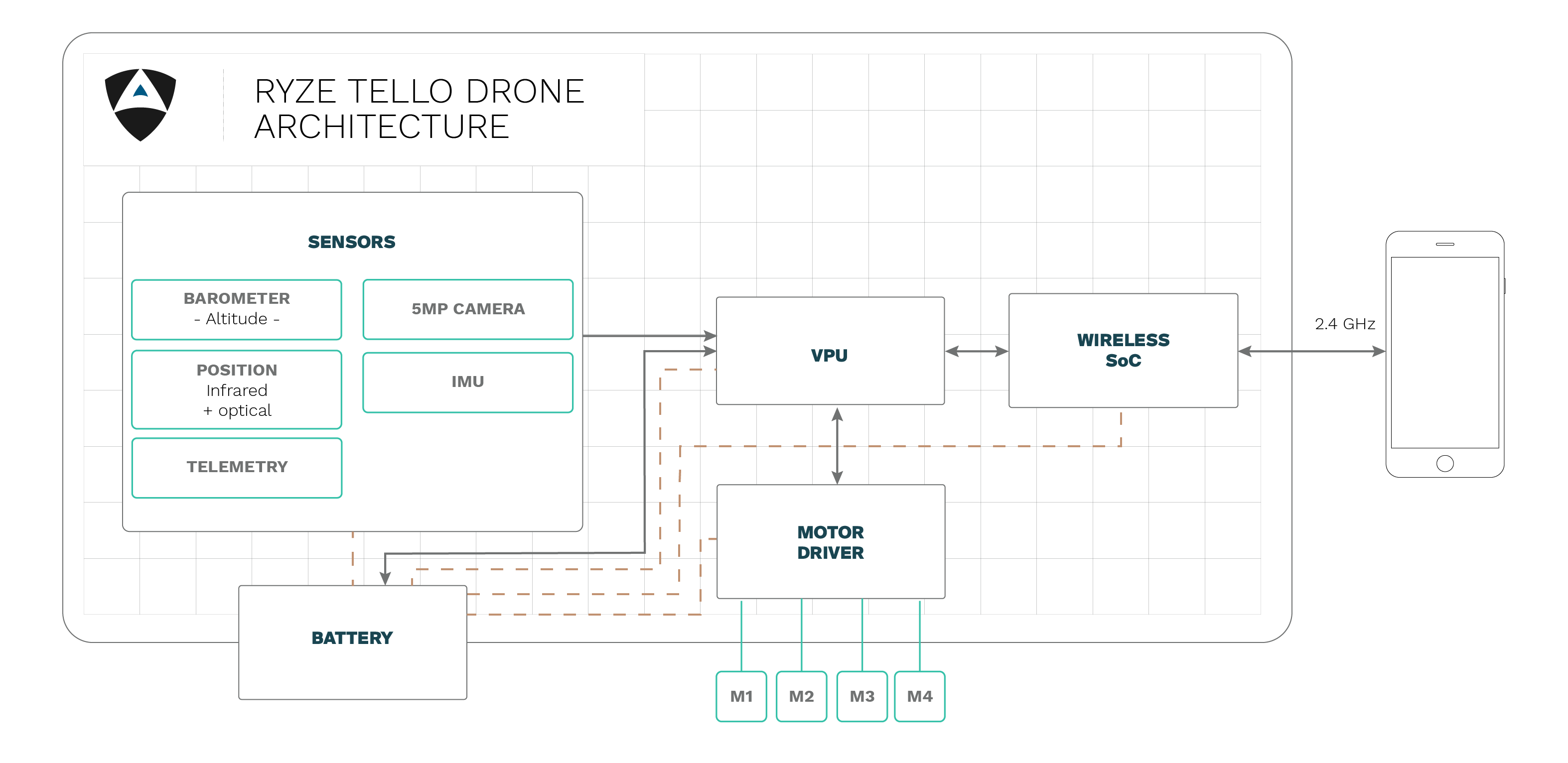
The Ryze Tello is a drone manufactured in collaboration with DJI in terms of internal components and an
14-core Intel VPU manufactured by Movidius.
With an approximate weight of 80 grams, and an autonomy of about 13 minutes. Is both nimble and stable at
low altitudes. This is achieved by an infrared system capable of measuring its distance in respect with the
ground as well as a small camera to have a visual reference of its place, both located in the belly of the
device.
It has a best case scenario max driving distance of 100 meters, and a current virtual ceiling of 30 meters,
although this limit was increased in the past via firmware updates.
The peak velocity on its fast mode is about 28 km/h
When powered, it creates a wireless network without a password of any kind to which we connect our
control device and then start the Tello application.
Since it doesn't force the user to establish a password neither it does not create a unique bind of any kind
between the two devices is trivial to hijack it with a minimal investment in hardware and basic knowledge.
Today we make a vulnerability public through this report.
This vulnerability is widespread in consumer electronics and can be used by a malicious operator to greatly
impact your privacy.
We encourage you to reach out if you are concerned about the privacy impact this may pose.

Our pentesting methodology for Tello considered the following 9 steps as depicted below:
Learn more about pentesting robots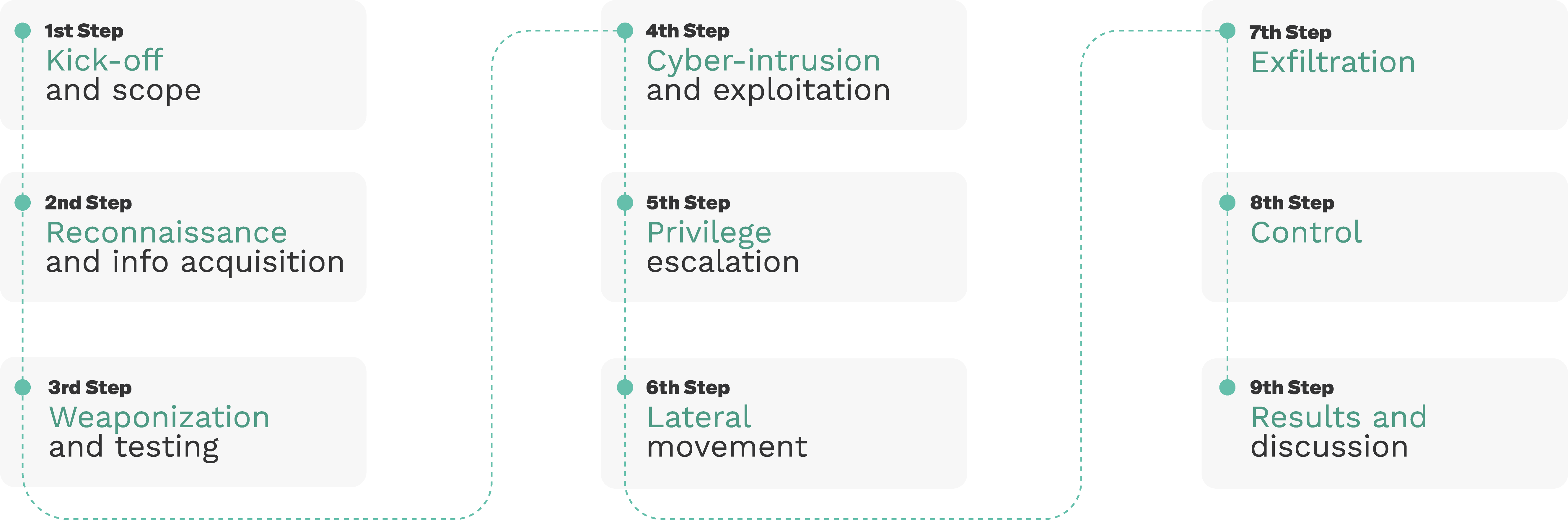
RVDP#1208
Our research has shown us that time after time security of IoT devices and consumer grade electronics is
left aside for the sake of making the device easier to use. But Hobbyists, Consumers and drone enthusiasts
don't have to be Cybersecurity experts.
The fact that security is not considered at the inception of the product is what this is all about. We have
safety standards for almost everything, and our vision is that in the future everything will have to comply
with a security standard as well. Before it leaves the factory. Pushing this responsibility to the end user is
not good enough.
From Alias Robotics, we will insist on receiving the latest updates and plan to react based on the
manufacturer’s response to the current insecurity landscape while requesting to enforce European laws.

At Alias Robotics we encourage a security-first approach to robotics. One that focuses on continuous monitoring and management of robot security risks and threats, leveraging modern tools and automation techniques to ensure that, at all times, the robots stay safe and secure. As indicated in the past, we strongly believe that vulnerability disclosure is a two-way street where both vendors and researchers, must act responsibly. We strongly believe each security researcher or group should reserve the right to bring deadlines forwards or backwards based on extreme circumstances.
Alias remains committed to treating all vendors strictly equally and we expect to be held to the same standard. By no means Alias encourages or promote the unauthorized tampering with running robotic systems. This can cause serious human harm and material damages.