



This study presents a short sneak peek into the penetration testing activity that we conducted on Pepper and NAO robots from Softbank Robotics. Following a security research approach, our team identified security threats and provided guidance to customers on how to address security issues and mitigate them on these robots. Developed in the context of a commercial application, this robotic case study takes place in an arbitrary service-oriented setting, characterized by an environment where the robot collaborates and works together with human professionals serving customers.
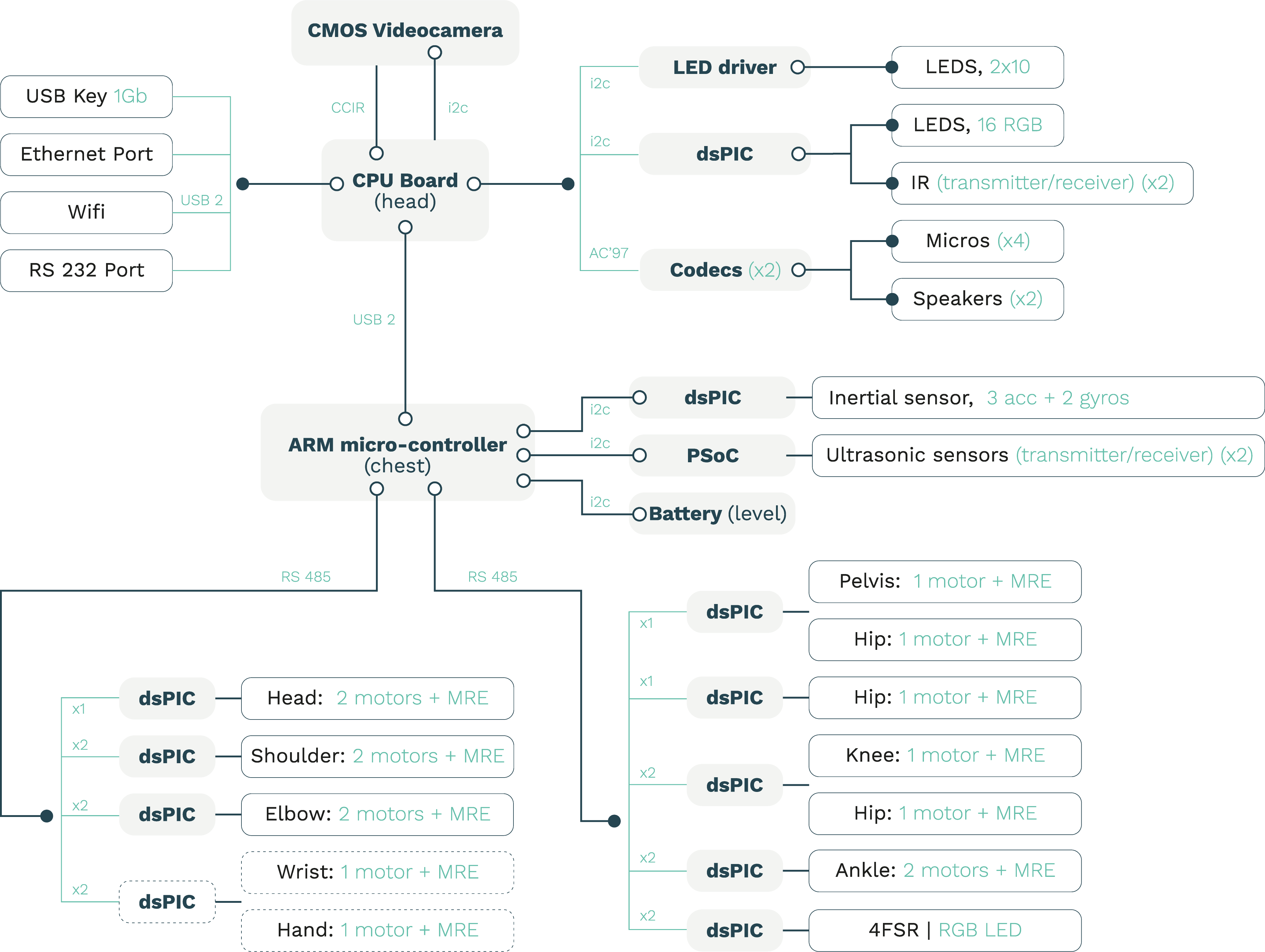
While several flaws apply to both robots, our short recap in here focuses heavily on Pepper, a semi-humanoid robot designed with the ability to detect emotion analyzing expressions and voice tones. The robot's head has four microphones, two HD cameras (in the mouth and forehead), and a 3D depth sensor (behind the eyes). There is a gyroscope in the torso and touch sensors in the head and hands. The mobile base has two sonars, six lasers, three bumper sensors, and a gyroscope.
Pepper is designed to be highly interactive, however, cyber security has barely been considered in its development. This fact became evident from our research, which complements previous work and raises additional concerns. Thanks to the permission for disclosure, we hereby leave a partial report of our findings and ultimately encourage end-users to carefully consider the privacy of their customers when they are exposed to these insecure robots.


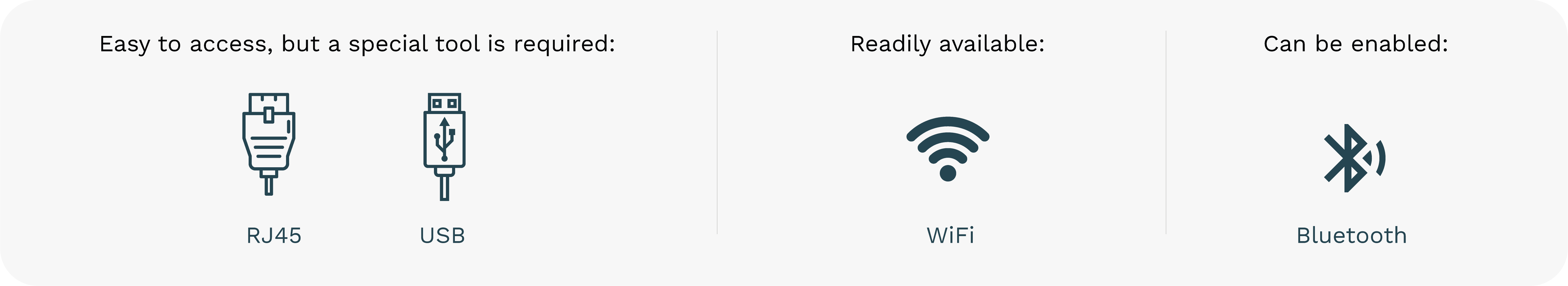

Either by social or technical means the bad actor gains access to the network. One of the easiest methods involves using WPS. A feature is available in many commercial access points that is usually enabled by default by the ISPs. The footprinting of this is trivial since it is usually announced alongside the SSID of the network on a mobile device. Pixiedust is used to brute force the WPS PIN and gain access to the network.
If you have physical access to the robot you can go ahead and ask it for their IP address the robot will happily oblige. Within the network either typing the ip or nao.local into a web browser will take you to the Web interface. In this case NMAP is used to scan the whole network and get the IP address and services of the robot.
Form here we only need to gain access via ssh since the ssh password and web server is the same. Hydra used with a custom wordlist loaded to perform a dictionary attack. Both the reconnaissance phase (NMAP) and the exploit phase (Hydra) can be combined and be left unattended with a tool like Sparta, further enhancing a covert attack.
As previously discussed strong authentication methods and proper access control should be paramount in social robots. From the high risk to intimacy and information breach from a robot like NAO, to the human and material threats a robot
like Pepper pose.
Standing at 120cm tall (4 ft) and equipped with functional human like hands and arms, cameras and microphones, a rogue robot like Pepper can be able to...
• Steal passwords/credit card information • Open and close doors • Activate fire alarms • Push buttons, turn dials, etc... • Turn on and off machines
• Carry small objects • Generate floorplans via SLAM • Spy on conversations • Record video and pictures • Manipulate light tools such as knifes/scalpels
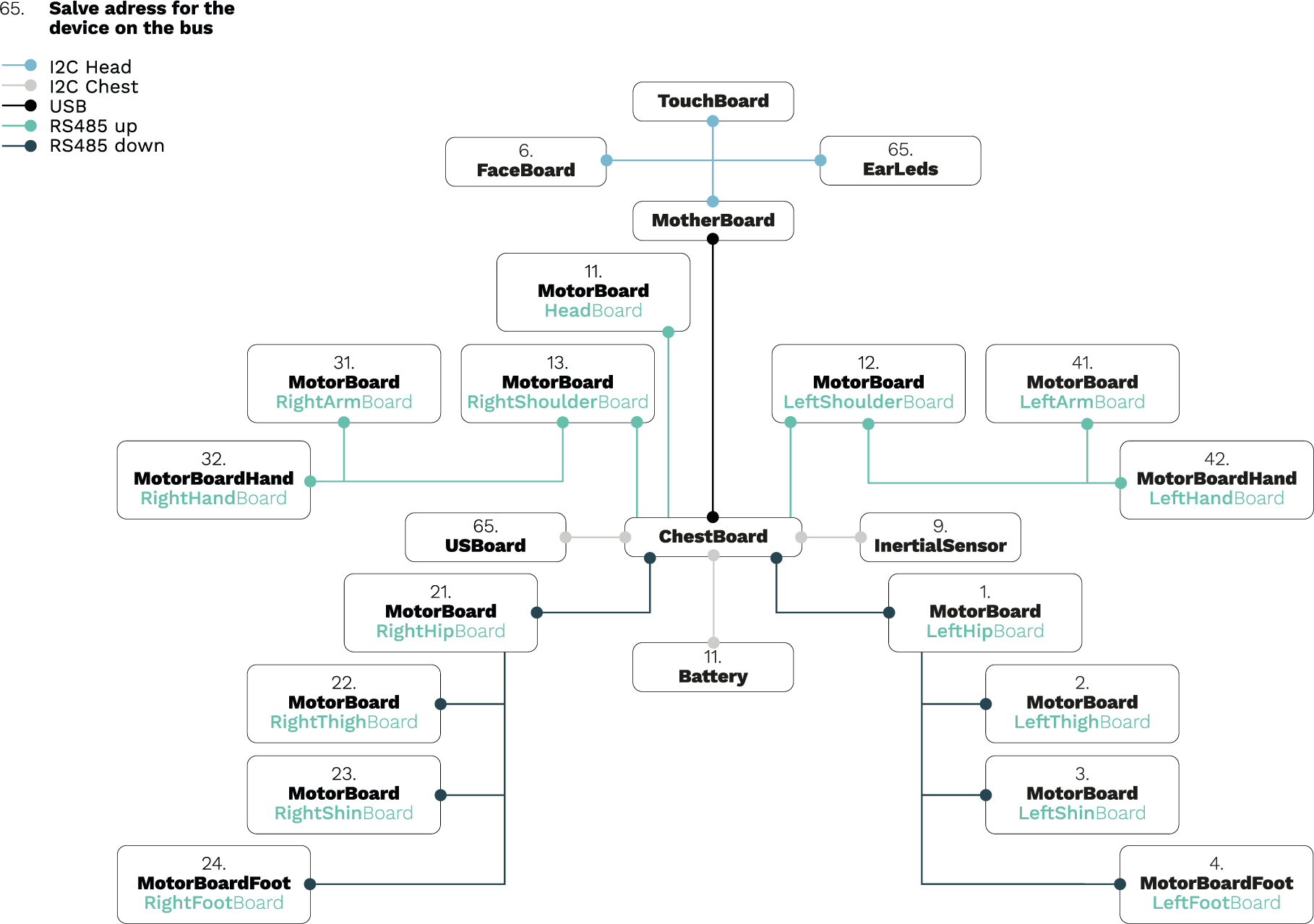
RVD #537
The Default User (NAO) for the robot has a wide arrange of privileges including ssh access and configuration via browser. even though the user is prompted to change the password on first use, the user cannot be modified and there is no strength requirements for the password making it more vulnerable to a brute force attack. More so the default Credentials to the robot are publicly available on the user manual. If not secured properly a Bad actor within the same network as pepper/nao can do any of the following:
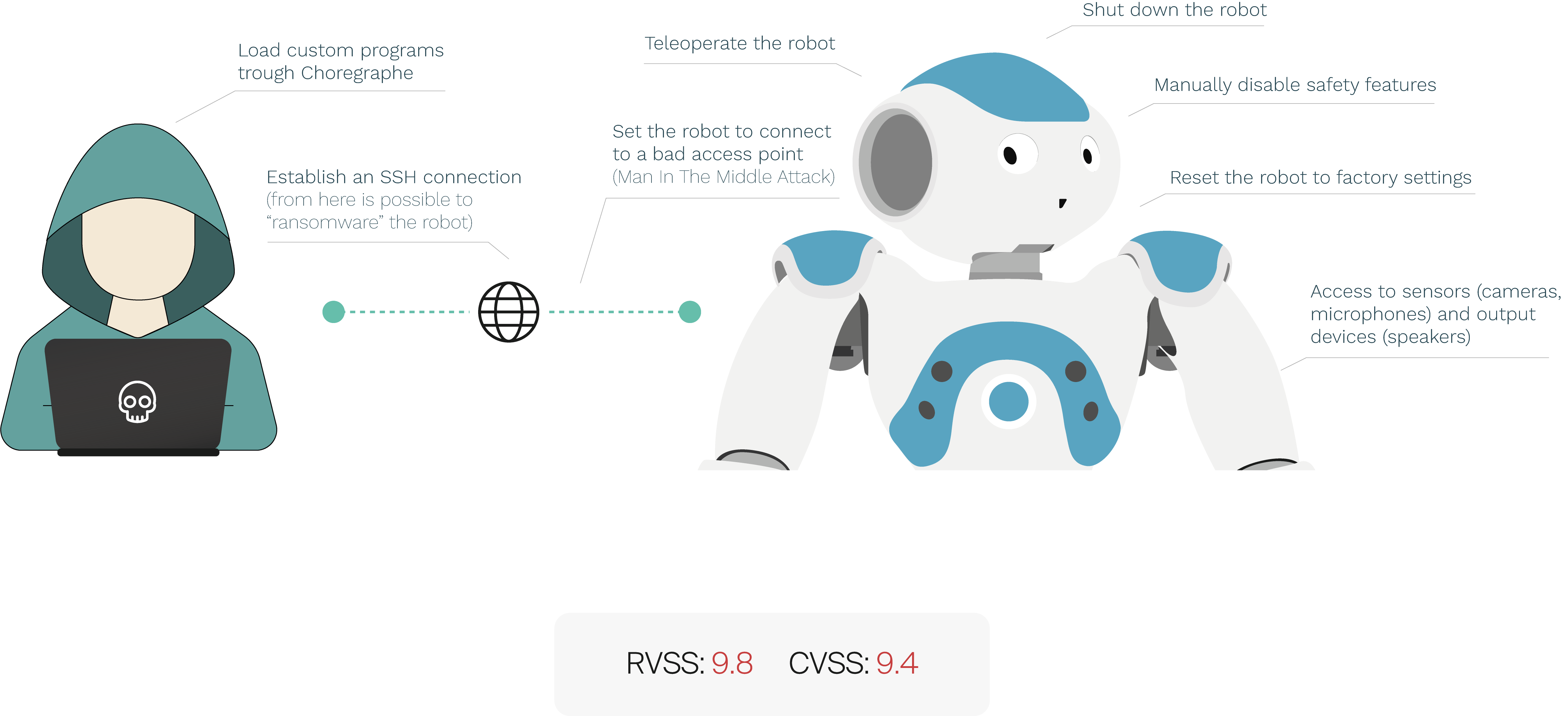

✱ We feel this is troubling in any setting but especially around children, elders and in healthcare environments in which a robot like pepper that is equipped with human like hands is able to some degree to operate tools intended for humans.
RVD#9
RVD#12
RVD#14
We truly believe that a robot like Pepper can be a invaluable tool to help society however in order to do so effectively and without putting humans and environments at risk, we first encourage mitigation of the many and already publicly known security issues present. As of 2018, more than 12.000 Pepper robots were sold in Europe alone. We discourage the use of this robot "as is" and proactively recommend a careful security assessment of applications involving such robots.