



The Unitree G1 humanoid robot, marketed as an advanced consumer robotics platform starting at $16,000, contains critical privacy violations and security vulnerabilities that expose users to unprecedented surveillance risks. Through comprehensive security analysis using the CAI (Cybersecurity AI) framework, researchers discovered that these robots continuously transmit sensitive telemetry data to servers in China and elsewhere without user consent or notification.
The investigation revealed critical security flaws in the robot's BLE provisioning protocol, which contains a command injection vulnerability allowing root access via malformed Wi-Fi credentials, exploitable using hardcoded AES keys shared across all units. Partial reverse engineering of Unitree's proprietary FMX encryption revealed a static Blowfish-ECB layer and a predictable LCG mask—enabling inspection of the system. Beyond these technical vulnerabilities, the G1 robot actively collects and transmits audio from varioius sensors and actuators including complete motion telemetry from 20+ motors. Most alarmingly, critical security credentials including RSA private keys are stored with world-writable permissions, while SSL certificate verification is disabled in communication protocols. These findings demonstrate a severe violation of European GDPR and international privacy laws, positioning these humanoid robots as potential surveillance devices in homes and workplaces.
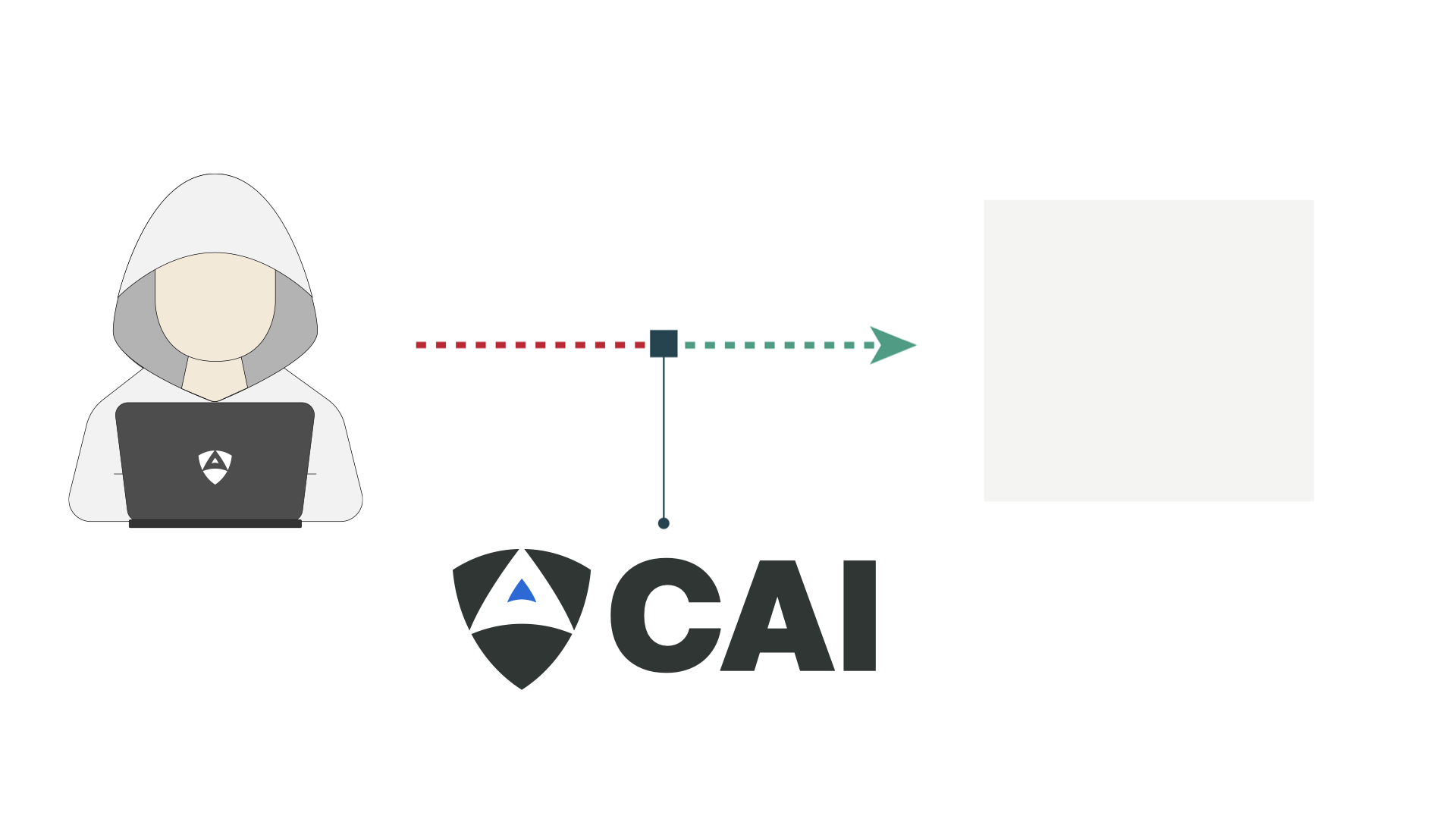

This video demonstrates the CAI (Cybersecurity AI) framework exploring the Unitree G1 humanoid robot's infrastructure and discovering some of the upstream connectors that lead to critical privacy violations. The footage shows various infringing upstream connections that violate GDPR and international privacy laws.
CAI is the leading open-source framework to democratize advanced security testing through specialized AI agents. With EU-backing, CAI is used by thousands of security researchers and organizations worldwide. Robots are systems of systems and their complexity difficults cybersecurity testing. Tools like CAI are essential to assess the security of these systems. Robots like the Unitree G1 are just one of the many use cases for CAI in robotics.
By 2028, most cybersecurity actions will be autonomous, with humans teleoperating, making CAI's approach to AI-powered vulnerability discovery increasingly critical for organizational security.
The Unitree G1 is an advanced humanoid robot developed by Unitree Robotics, a Chinese company founded in 2016 that has rapidly become a leader in legged robotics. Standing at 1.27 meters tall and weighing approximately 35kg, the G1 robot features 23-43 degrees of freedom depending on configuration, with prices starting at $16,000 USD. It represents one of the most affordable humanoid platforms available for research and development, capable of walking at speeds up to 2 m/s and performing complex movements including jumping 1.4 meters high.
Equipped with six Intel RealSense depth cameras, 3D LiDAR, dual microphones, and comprehensive sensor arrays, the G1 robot is marketed for applications in research, education, and service industries. However, our security analysis reveals that this sophisticated sensor platform continuously transmits telemetry data to servers in China without user consent, including audio streams, video feeds, GPS location, and complete motion data from all motors. These privacy violations, combined with critical security vulnerabilities such as world-writable RSA private keys and disabled SSL certificate verification, position these robots as potential surveillance devices that violate GDPR and international privacy laws.
27
3.45 €
The Unitree G1 humanoid robot is popular and widely used robot for humanoid manipulation tasks but presents a complex security challenge: these consumer robots continuously transmit comprehensive telemetry to China-related servers without user knowledge or consent. The investigation revealed unauthorized processing of audio from dual microphones, video from six cameras, GPS location data, and telemetry submission from 20+ actuators. Critical findings included RSA private keys stored with world-writable permissions (chmod 666), disabled SSL certificate verification, and hardcoded credentials. The robots maintain persistent MQTT connections on port 17883 to servers at 43.175.228.18, transmitting data encrypted with static Blowfish keys, violating GDPR Article 7 (consent) and Article 25 (data protection by design).
Using the CAI (Cybersecurity AI) framework, researchers conducted a comprehensive security audit of the G1 robot's communication protocols and data collection practices. CAI successfully reverse-engineered the two-layer encryption system, breaking the static Blowfish layer and identifying the hardware-bound LCG algorithm. Analysis of 20+ ROS2/DDS topics revealed real-time transmission of sensitive data including audio streams (rt/audio_msg), video feeds (rt/frontvideostream), and AI conversation history (rt/gpt_state). The framework documented evidence of continuous surveillance capabilities, providing concrete proof for regulatory compliance violations and enabling users to understand the privacy risks posed by these humanoid robots in their environments.
